China rebukes Singapore media after Minister links cyberattacks by UNC3886 to Beijing
China’s Embassy in Singapore has criticised media reports that linked cyberattacks by UNC3886 to China. The reports were based on statements by Minister K Shanmugam, who described the group as a serious national security threat.
- Singapore Minister K Shanmugam identified UNC3886 as a serious cyber threat, citing Mandiant’s assessment of the group as China-linked.
- He warned that attacks on critical infrastructure could enable espionage or widespread disruption.
- CSA confirmed UNC3886 activity has been detected and is under investigation, with all critical sectors on alert.
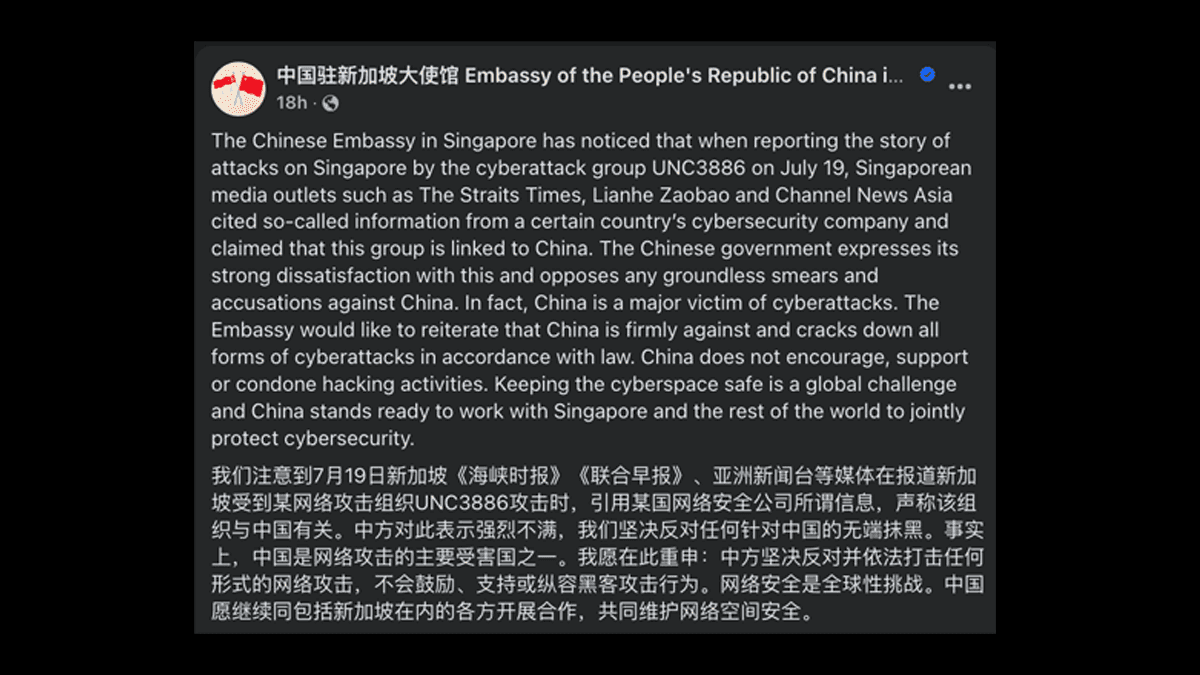
- China’s Embassy condemned the media reports as baseless, asserting China is a frequent victim of cyberattacks.
The Chinese Embassy in Singapore has voiced strong objections to local media reports suggesting that cyber espionage group UNC3886, believed to be behind recent cyberattacks on Singapore, is linked to China.
The embassy’s response was issued on 19 July 2025 via two separate Facebook posts, following widespread media coverage based on remarks made by Singapore’s Coordinating Minister for National Security and Minister for Home Affairs, K Shanmugam, on 18 July.
Mr Shanmugam, speaking at a dinner commemorating the 10th anniversary of the Cyber Security Agency of Singapore (CSA), stated that Singapore is confronting a “highly sophisticated threat actor” targeting the nation's critical infrastructure.
He identified the actor as UNC3886, citing cybersecurity firm Mandiant—owned by Google—which has labelled the group a “China-nexus espionage group”. He warned that UNC3886 poses a grave threat to Singapore’s national security, stating that a successful attack could result in widespread disruption or enable espionage operations.
According to Mr Shanmugam, UNC3886 operates with advanced capabilities that allow it to evade detection and maintain long-term access in compromised systems. The group has reportedly been linked to cyberattacks on critical sectors in both the United States and Asia, including defence, telecommunications, and infrastructure.
The minister elaborated on the growing danger posed by advanced persistent threats (APTs), noting that between 2021 and 2024, suspected APT-related attacks on Singapore surged more than fourfold.
While he did not disclose operational details for security reasons, Mr Shanmugam revealed that UNC3886 had infiltrated parts of Singapore’s critical information infrastructure. He stressed that attackers are not only targeting government and industrial systems but also exploiting external vendors, supply chains, and even residential devices such as home routers and baby monitors.
The CSA confirmed that it is leading the investigation into the UNC3886 activity. It stated that it is coordinating with affected organisations and monitoring all essential sectors, including energy, water, finance, healthcare, transport, government, media, and emergency services.
“These attacks are often protracted campaigns,” said CSA in a statement, “and withholding details is necessary at this stage to preserve operational security.”
Mr Shanmugam also provided context by referencing other APT groups identified by international cybersecurity agencies. These include Salt Typhoon, allegedly linked to China’s Ministry of State Security, and Volt Typhoon, reportedly tied to the People’s Liberation Army. Both groups have been connected to attacks on US utilities and infrastructure.
He mentioned Silk Typhoon, a lesser-known group allegedly targeting diplomatic data and trade secrets. Reported victims include ministries in Spain and Finland, and media organisations in Japan, South Korea, and the United States.
The minister highlighted an incident in October 2024, where 10 websites mimicking legitimate Singaporean domains were blocked. These were believed to be created by foreign actors for potential hostile information campaigns.
Additionally, in 2024, more than 2,700 Singapore-based devices were compromised in a global botnet attack involving home devices. M
He underscored the cascading impact of cyberattacks, warning that a single hit on power systems could trigger failures in transport, healthcare, water, air travel, and financial sectors.
Singapore, he said, must review its supply chain security and avoid working with untrustworthy technology partners. “We have to be realistic,” Mr Shanmugam said. “Even technologically advanced countries have not been able to prevent such attacks completely.”
He concluded that Singapore must continue to invest in strong cyberdefences, build resilience, and develop containment strategies to safeguard national security.
The Chinese Embassy, in its 19 July response, criticised the reports linking UNC3886 to China as “groundless smears” and objected to the reliance on assessments from “a certain country’s cybersecurity company”.
“The Chinese government expresses its strong dissatisfaction with this and opposes any groundless smears and accusations against China,” said the embassy. It reiterated China’s position that it neither supports nor condones hacking activities, and that it is in fact one of the world’s primary victims of cyberattacks.
The embassy cited several incidents, including over 270,000 cyberattacks from abroad on Chinese systems during the 9th Asian Winter Games in early 2025, and over 1,300 APT attacks reported in 2024 by 360 Security Technology Inc.
Chinese government agencies, research institutions, the defence sector, and transportation networks were among the most heavily targeted, according to the embassy.
China called for global cooperation to safeguard cybersecurity, and expressed willingness to work with Singapore and other nations in addressing common challenges in cyberspace.








0 Comments